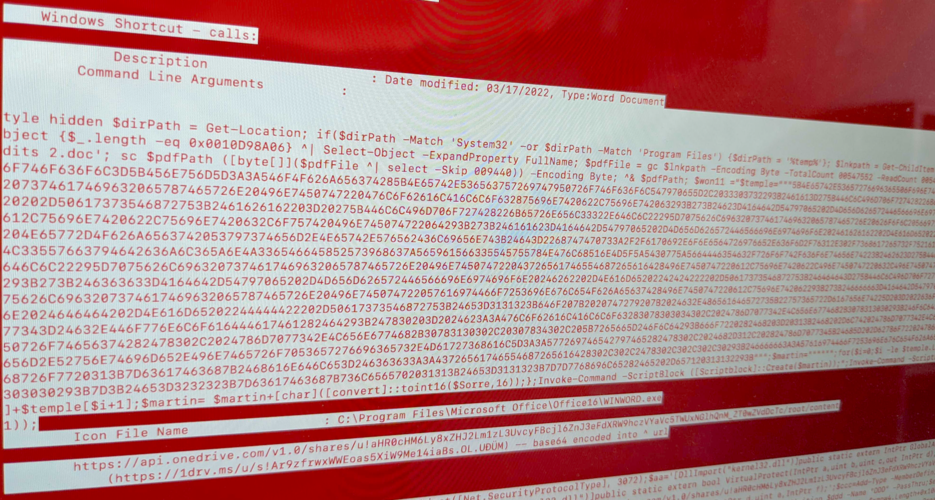
Hackers linked to North Korea appear to have broken into the private computer of a former South Korean intelligence official as part of an effort to target journalists with a previously unknown type of malware, an NK News investigation with cybersecurity firm Stairwell revealed.
After gaining access to the email account of a former director at South Korea’s National Intelligence Service (NIS), the attackers copied the content of past conversations with the official to send spoofed emails from a similar-looking address — [email protected] — to NK News founder Chad O’Carroll. The tactic allowed the hackers to avoid using the intelligence official’s real email account to send emails and risk detection, while making the malicious lures more believable.
Hackers linked to North Korea appear to have broken into the private computer of a former South Korean intelligence official as part of an effort to target journalists with a previously unknown type of malware, an NK News investigation with cybersecurity firm Stairwell revealed.
After gaining access to the email account of a former director at South Korea’s National Intelligence Service (NIS), the attackers copied the content of past conversations with the official to send spoofed emails from a similar-looking address — [email protected] — to NK News founder Chad O’Carroll. The tactic allowed the hackers to avoid using the intelligence official’s real email account to send emails and risk detection, while making the malicious lures more believable.
Become a member for less
than $5.75 per week.
Unlimited access to all of NK News: reporting, investigations, analysis
The NK News Daily Update, an email newsletter to keep you in the loop
Searchable archive of all content, photo galleries, special columns
Contact NK News reporters with tips or requests for reporting
Get unlimited access to all NK News content, including original reporting, investigations, and analyses by our team of DPRK experts.
Subscribe now
All major cards accepted. No commitments – you can cancel any time.